Facebook bug could have allowed attacker to take over accounts
A vulnerability in Facebook could have allowed an attacker to take over a Facebook account without the victim needing to click on anything at all.
The bug was found by a bounty hunter from Nepal called Samip Aryal and has now been fixed by Facebook.
In his search for an account takeover vulnerability, the four times Meta Whitehat award receiver started by looking at the uninstall and reinstall process on Android. By using several different user agents he encountered an interesting response in the password reset flow.
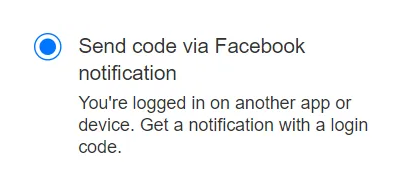
After investigation, a few characteristics of the login code made it an interesting attack vector:
- The code was valid for two hours
- It did not change during that period when requesting it
- There was no validation if you attempted a wrong login code
Combined with the fact that these codes are only 6 digits, Samip saw opportunities for a brute force attack, where an attacker repeatedly tries to access login credentials in the hope of eventually getting into an account.
After uncovering all this information, and with his extensive knowledge about the Facebook authentication process, Samip found the method to take over an account was relatively simple:
- Pick any Facebook account.
- Try to login as that user and request a password reset (Forgot password).
- From the available reset options choose “Send code via Facebook notification”.
- This creates a POST request. As part of a POST request, an arbitrary amount of data of any type can be sent to the server in the body of the request message.
- Copy that POST request and use a method to try all the 100,000 possibilities. Note, 100,000 possibilities may sound like a lot, but given the two hour time-frame there are plenty of options to do that.
- The matching code responds with a 302 status code, a redirect that confirms the search was successful.
- Use the correct code to reset the password of the account and the attacker can now take over the account.
There was one caveat. The owner of the account will see the notification on the device they are logged in with. And strangely enough the notifications came in two flavors.
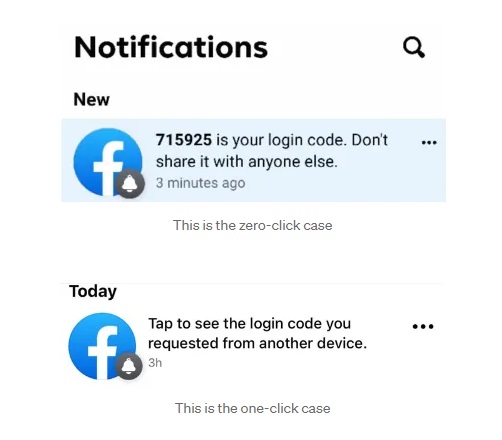
The difference in notification which makes it a zero-click or not
The first one works as described above, but the second one does require the account owner to tap that notification before Facebook generates a login code. That makes it a lot harder to take over the account.
A detailed report of how Samip found the vulnerability is available on his Medium page.
Facebook has awarded Samip a bounty and fixed the issue. Together with other bounty hunters, Samip submitted hundreds of reports to Meta which they resolved, making Facebook and other platforms a safer place along the way.
Paying attention pays off
There are a few takeaways from this method that Facebook users, and users of other platforms for that matter, might use to their advantage.
- Pay attention to the signs that a password request has been initiated (email, notifications, texts, etc.) Somebody could be trying to take over your account. Follow the instructions on the password reset notification if it’s not you doing the reset.
- Don’t use the Facebook login option on other platforms, and certainly not on ones that have personal or financial information about you.
- Turn on 2FA for Facebook to make it harder for criminals to hijack your account.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
