Ransomware gang files SEC complaint about victim
In what seems to be a new twist on the ransomware theme, the notorious ALPHV/BlackCat ransomware group has filed a complaint with the US Securities and Exchange Commission (SEC) about the software company MeridianLink.
ALPHV is one of the most active ransomware-as-a-service (RaaS) operators and regularly appears in our monthly ransomware reviews. MeridianLink supplies “digital lending solutions” to banks, credit unions, fintechs, and other financial institutions.
Since September 5, 2023 the SEC has required public companies to disclose within four days all cybersecurity breaches that could impact their bottom lines. Apparently ALPHV is aware of the new rules and in this screenshot of the SEC complaint form it wrote:
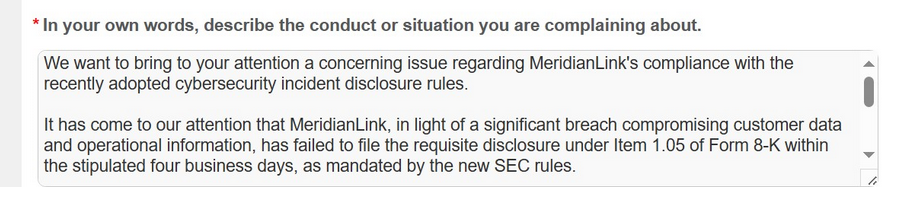
“We want to bring to your attention a concerning issue regarding MeridianLink’s compliance with the recently adopted cybersecurity incident disclosure rules.
It has come to our attention that MeridianLink, in light of a significant breach compromising customer data and operational information, has failed to file the requisite disclosure under Item 1.05 of Form 8-K within the stipulated four business days, as mandated by the new SEC rules.”
The referenced item (Form 8-K Item 1.05) states:
“Registrants must disclose any cybersecurity incident they experience that is determined to be material, and describe the material aspects of its:
– Nature, scope, and timing; and
– Impact or reasonably likely impact.
An Item 1.05 Form 8-K must be filed within four business days of determining an incident was material. A registrant may delay filing as described below, if the United States Attorney General (“Attorney General”) determines immediate disclosure would pose a substantial risk to national security or public safety.
Registrants must amend a prior Item 1.05 Form 8-K to disclose any information called for in Item 1.05(a) that was not determined or was unavailable at the time of the initial Form 8-K filing. “
As you can see, there are possible exceptions and for all we know, the investigation into the nature and gravity of the data breach is still ongoing. Or far from as material as ALPHV wants us to believe.
In a statement to databreaches.net MeridianLink said:
“Safeguarding our customers’ and partners’ information is something we take seriously. MeridianLink recently identified a cybersecurity incident that took place on Nov 10. Upon discovery on the same day, we acted immediately to contain the threat and engaged a team of third-party experts to investigate the incident. Based on our investigation to date, we have identified no evidence of unauthorized access to our production platforms, and the incident has caused minimal business interruption.
We have no further details to offer currently, as our investigation is ongoing.”
Apparently the ransomware operators like to pretend that what they are doing is their civic duty. This tile is posted on the landing page of the gang’s leak site.

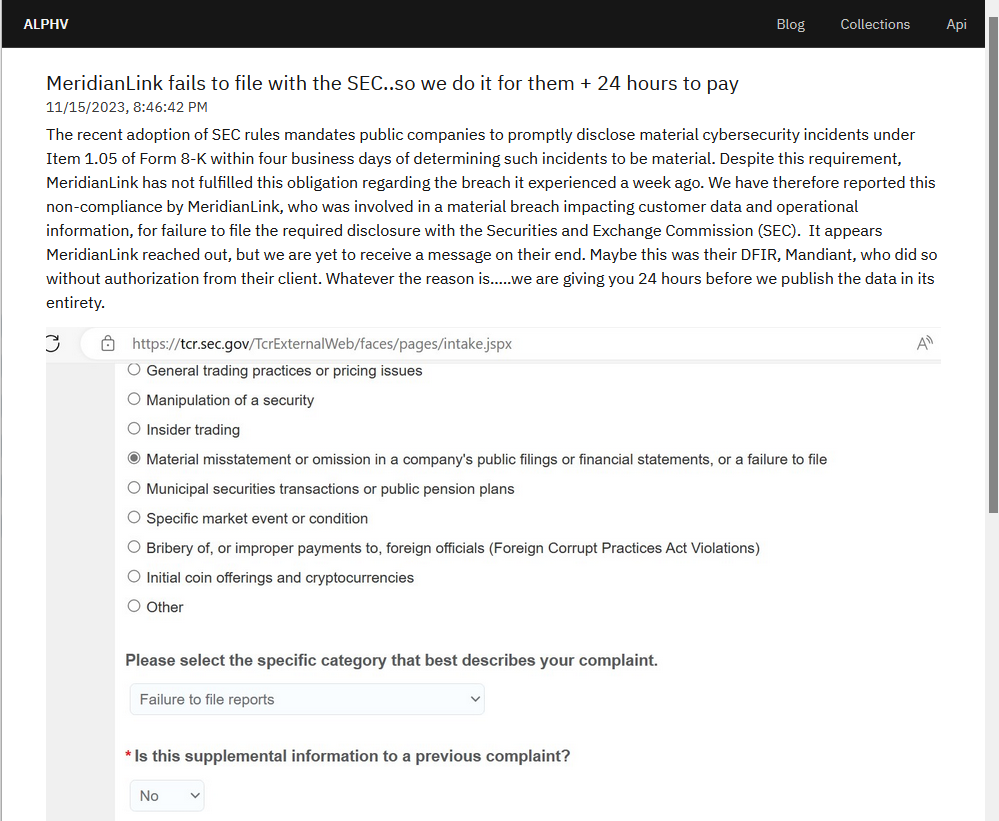
Clicking through, we found the screenshot of the form and a non-explanatory statement why they filled the form out.
“Despite this requirement, MeridianLink has not fulfilled this obligation regarding the breach it experienced a week ago. We have therefore reported this non-compliance by MeridianLink, who was involved in a material breach impacting customer data and operational information, for failure to file the required disclosure with the Securities and Exchange Commission (SEC). It appears MeridianLink reached out, but we are yet to receive a message on their end. Maybe this was their DFIR, Mandiant, who did so without authorization from their client. Whatever the reason is…..we are giving you 24 hours before we publish the data in its entirety.”
Whatever the reason is behind MeridianLink’s apparent decision not to report the cyber-incident (yet), the action taken by ALPHV certainly is something we haven’t seen before. It may be a warning or an attempt to gain extra leverage. Knowing how hard it can be to determine the scope of a cyberattack in just a few days, we can expect to see this happen more often.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
